- What is end-to-end encryption?
- End-to-end encryption is a method to encrypt data in the source node and to decrypt data in the destination node. The security of data won't be affected by the intermediate node.
- PriKey which is generated by the client will be used to encrypt all data sent with BAT. It can't be decrypted by any third party include the developer.
- How does BAT ensure security?
- Tunnel Encryption
- Content Encryption
- Server Database Security
- Keys Security
- More details about BAT's encryption algorithms
- A. Tunnel encryption
- What encryption algorithms does Bat use?
- RSA, ECDHE, AES256_CBC, SHA256, SHA1 used in tunnel encryption.
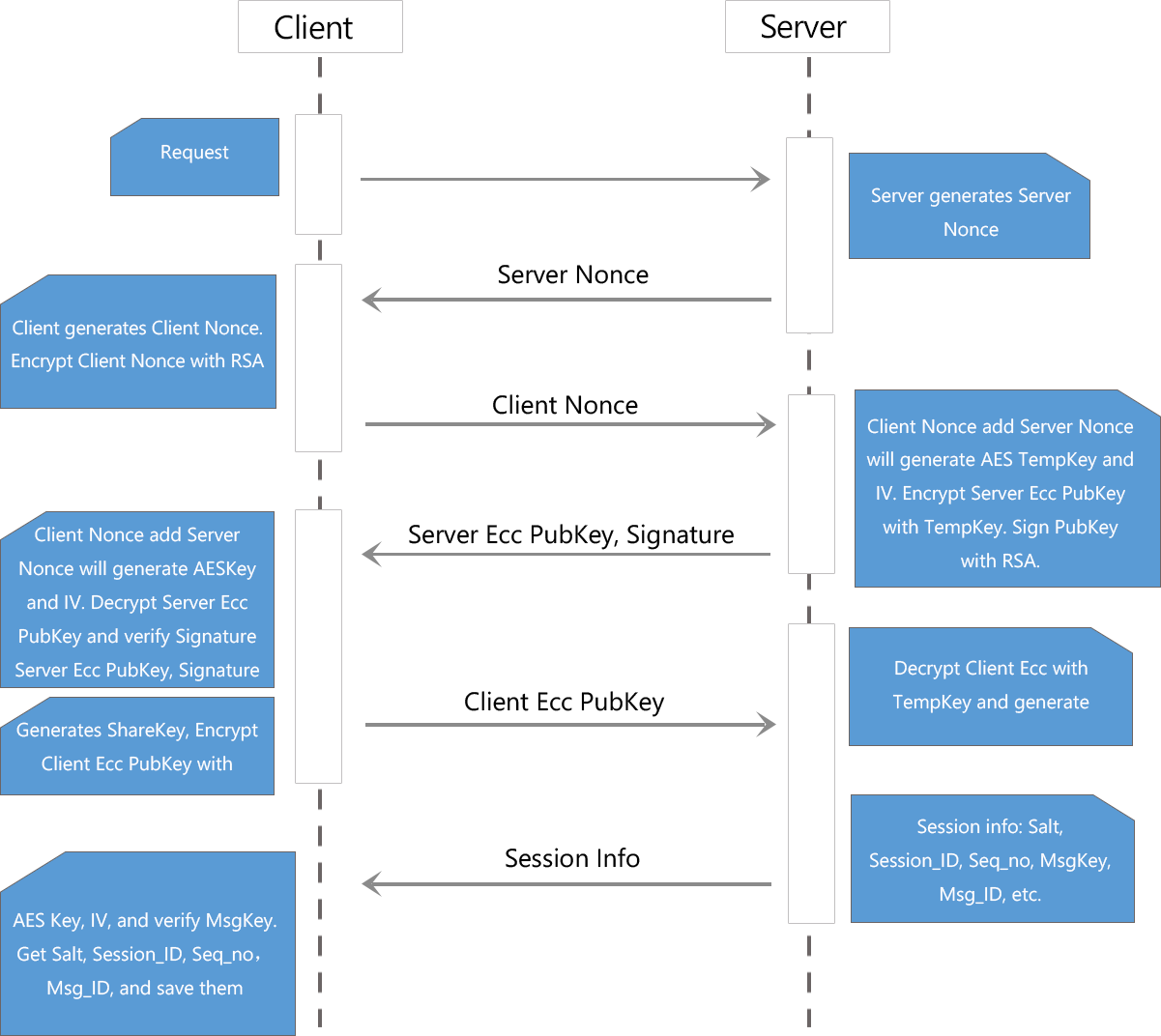
- Steps:
- 1.The client and server generate a nonce respectively.
- 2.The server sends its nonce to the client.
- 3.The client will encrypt its nonce by RSA and send it to the server.
- 4.The server will decrypt the client's nonce by RSA, which can prevent man-in-the-middle attacks.
- 5.The client's nonce adds the server's will generate TempKey and TempIV (the client and server have the same TempKey and TempIV)
- 6.The client and server will generate their PriKey and PubKey pair respectively by ECDHE.
- 7.The client will encrypt its ECDHE PubKey by TempKey and TempIV, then send it to the server.
- 8.The server will decrypt the ECDHE PubKey sent from the client.
- 9.The server will encrypt its ECDHE PubKey by TempKey and TempIV. And RSA will create a digital signature on it. The ECDHE PubKey and the RSA digital signature will be sent to the client.
- 10.The server will generate ShareKey by ECDHE, the client's ECDHE PubKey and the server's ECDHE PriKey.
- 11.The client will decrypt the ECDHE PubKey and authenticate the digital signature sent from the server. ShareKey will be generated by the client's ECDHE PriKey and the server's ECDHE PubKey.
- 12.The server will initialize each parameter and send them to the client.The parameters include:
- AuthKeyID: It's a random client temperature identifier generated by the server.
- MsgKey:MsgKey will be generated after Sha256 encrypt the data which consists of ShareKey, AuthkeyID, MsgID, SessionID, Salt, SeqNo and real message content.The function of MsgKey:
- a. To prevent data tampering
- b. By working with ShareKey, aes256 key, IV can be generated, which can encrypt each message.
- MsgID: They can be messages and ID related to time. It can prevent replay attacks and deduplicate data.
- SessionID: It is a piece of data that is used in network communication. A session ID is typically granted to a visitor on their first visit to a site.
- Salt: In cryptography, a salt is random data that is used as an additional input to an one-way function that "hashes" data, a password or passphrase. Salts are used to safeguard passwords in storage.
- SeqNo: To prevent replay attack.
- 13.Each message has a different MsgID, SessionID, Salt, SeqNo and different message content. These data will cause a different MsgKey for each message each time. The changing MsgKey and ShareKey work together will generate a 32 bytes PriKey and IV for each message.
- 14.Key agreement would be processed again if ShareKey expired
- B. Content encryption's details
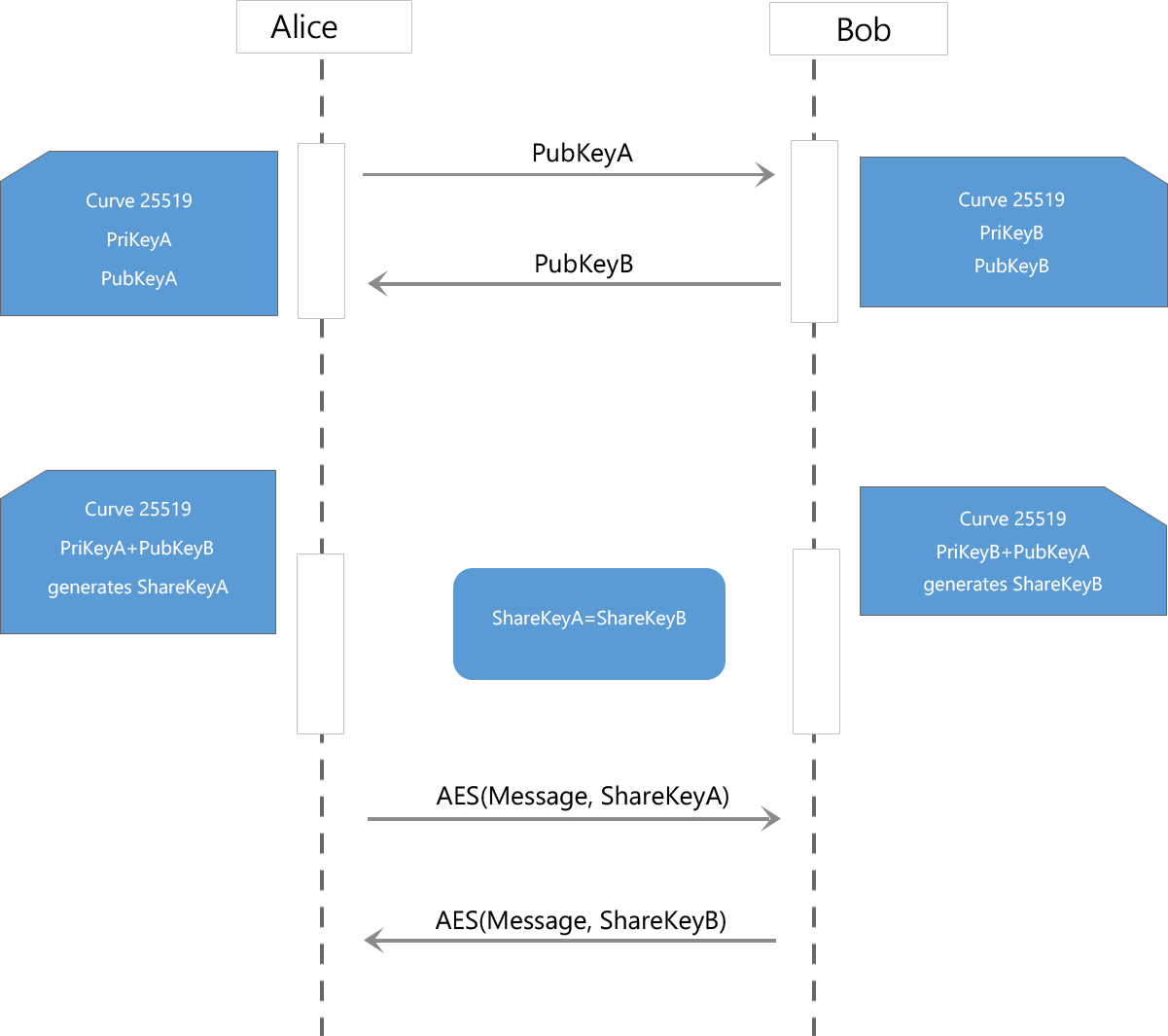
- Content encryption use the similar algorithms:
- 1.ECDHE PubKey and PriKey pair is generated and saved in the client.
- 2.PubKey will be sent to the server, and PriKey will be saved in the client.
- 3.When users sign in, they will receive all contact's message include their PubKey.
- 4.Send and receive messages will use ShareKey which is generated by user's PriKey and the opponent's PubKey.
- 5.Aes 256 PriKey will be generated by ShareKey for encryption and decryption.
- C. Database server security
- Database on the server can prevent man-made tampering.
- 1.There is a signature field in database.
- 2.ECDSA PubKey and PriKey pair is generated in database.
- 3.The server will generate or renew a signature by ECDSA when sensitive fields like password, userID, friend in database are added, deleted, and changed.
- 4.When these data such as password, userID, contact, etc., are read by the server, the ECDSA signature authentication will be triggered. The following process is allowed only by the right signature.
- 5.Server routines will be protected by signature and be encrypted.
- D. Keys security
- 1.SRP is used for all BAT passwords including login password, unlock passcode and auto login password, etc. These passwords are not stored on the server at all.
- 2.The PriKey will only be stored in users' phone.
- 3.Users can change their confidential code on the client at any anytime.
- What is PubKey and PriKey?
- PubKey is a public key while PriKey is a private key. They are generated in pair. Either of the keys can be used to encrypt a message; the opposite key of the pair is used for decryption.
- It is called asymmetric cryptography due to encrypt via PubKey and decrypt via PriKey. RSA and ECDHE are asymmetric cryptography which is mentioned above.
- How does asymmetric cryptography work?
- 1.A pair of PriKey and PubKey will be generated separately on Alice's client and Bob's client before they send any message.
- 2.PubKey is exchanged between Alice and Bob while PriKey is stored on the client.
- 3.If Alice would like to send a message to Bob, this message would be encrypted via PubKeyB.
- 4.Then Alice sends this encrypted message to Bob.
- 5.Bob will decrypt this message via PriKeyB as soon as it is received. Any other PriKey is invalid to decrypt this message.